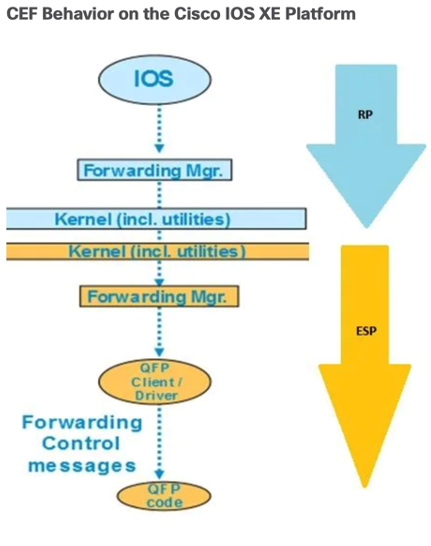
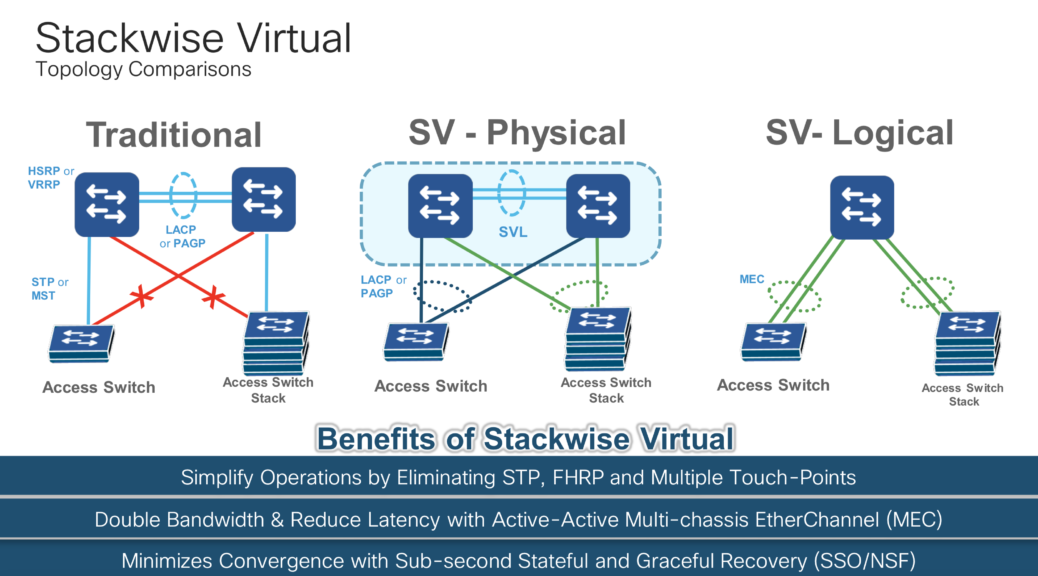
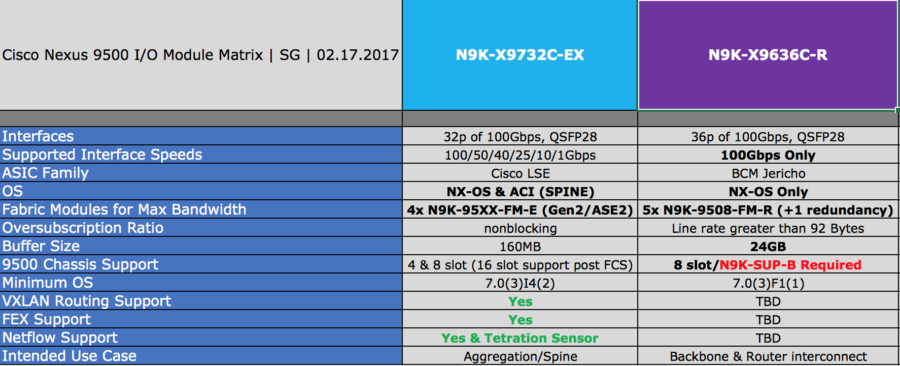
Cisco Express Forwarding (2023 Edition)
CEF Deep Dive (commands) for IOS-XE C9300 used as example Model: C9300L-24UXG-4X Control Plane (CP) = R0 Data Plane (DP) = F0, UADP/ASIC CEF Background: Why Cisco Express Forwarding (CEF)? “Necessity is the mother of invention” -proverb Let’s take a trip in the networking time machine back to simpler times (late 80s, early 90s). I’m going to start with the fundamentals of software-based forwarding and all the pipeline steps involved. We didn’t have fancy ASICs like we do today, so everything was done…